STEPS and INSTRUCTIONS
1. Create 1 cross-over cable, 1 straight-through cable and patch panel cable.
a. I consumed lots of time on this simple task due to the dullness of the crimping tools. Bring your own if you can.
b. Obviously, you’ll have to know the wiring standards of T568A and T568B to create the cables.
c. Every patch panel is different, so before taking the exam, visit the assessment center and check the patch panel type and color coding. The one I used had no color coding on it.
d. You must have every cable checked when finished at once by the assessor in order to move on.
2. Connect all the devices together using the cables.
2 desktops
1 switch
1 patch panel
1 wireless router
1 access point
1 laptop which will be connected wirelessly after configuring the router and the access point.
a. Drawing included in the reviewers.
** Additional cables will be provided
3. Once all devices are connected, get the mac addresses of the pc, server and laptop for the purpose of assigning them IP Addresses using DHCP reservations.
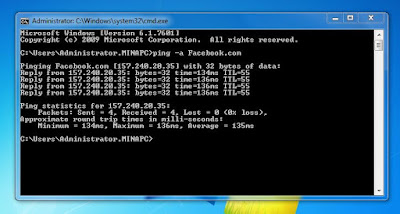
Note the mac addresses down together with the corresponding unit to avoid confusion. To get the MAC Address, open command prompt and type “getmac” or “ipconfig”.
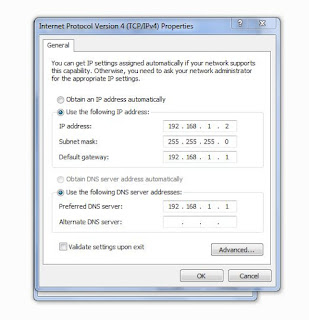
a. Here, although the devices are all configured to get IP addresses using DHCP, you will be instructed to select an IP address specifically that is why DHCP Reservations should be configured.
b. For example. Create a DHCP Pool of 192.168.1.100 to 192.168.1.200
c. From the pool, the IP 192.168.1.114 should be assigned to the pc
d. 192.168.1.117 should be assigned to the server
e. 192.168.1.155 should be assigned to the laptop
4. Configure the router using your web browser to access it's interface
a. In order to access the router’s interface, look for its IP address at the back of the device. If it’s not there, you can ask the assessor. If the router’s address is indicated on the back of the device but you are unable to access it using that address, reset first the router by pressing the power button for 10 to 20 seconds. Usually, the password to access the interface is indicated also on the device. Ask the assessor if otherwise.
b. Create the DHCP Pool as instructed; the ranges will be given by the assessor.
c. Change the SSID and configure wireless security using WPA2.
d. Configure DHCP reservations.
e. Check your work by pinging the connected devices, if task is accomplished, move on to the access point.
5. Configure the Access Point
a. Same steps as the router, you just have to change its SSID and IP configuration that corresponds with the IP subnet you are using.
6. Now, connect the laptop to the access point.
7. Test interconnectivity of all the devices by using the “PING” command. Make sure the devices got the correct IP addresses reserved to them.
8. Create folders on all the devices, share the folders and make sure everyone has read/write permissions.
9. Show your work to the assessor, he will give you instructions to test your work.
END OF module 2
COC3: Configuring Windows Server 2008 R2 or 2012
To be continued, edited and revised.